The other day I was “flipping” through Flipboard and came across an article on OSXDaily that discussed how one could prevent a Mac from automatically booting when the lid is opened.
The command to enable or disable this setting is quite simple. By leveraging Terminal, all you need to do is set the AutoBoot value.
Disable AutoBoot:
sudo nvram AutoBoot=%00
Enable AutoBoot:
sudo nvram AutoBoot=%03
While I personally like the AutoBoot feature, I can see why some people may choose to disable it; especially in an academic or corporate setting.
Using LANDESK Security Suite 2016, the NVRAM AutoBoot setting can easily be scanned for with every vulnerability scan, by building a custom definition to evaluate the NVRAM AutoBoot value. Then, using the repair logic, you can maintain a desired state in your organization even if an administrative user opts to change it.
And, the best part is, I’ve created the custom definition for you – no scripting needed on your behalf. Download the custom definition from GitHub here and import it to your core server.
Custom Definition Import
- Open the LANDESK console
- Go to Tools > Security and Compliance > Patch and Compliance
- From the definition types dropdown menu, ensure you have selected Custom definition
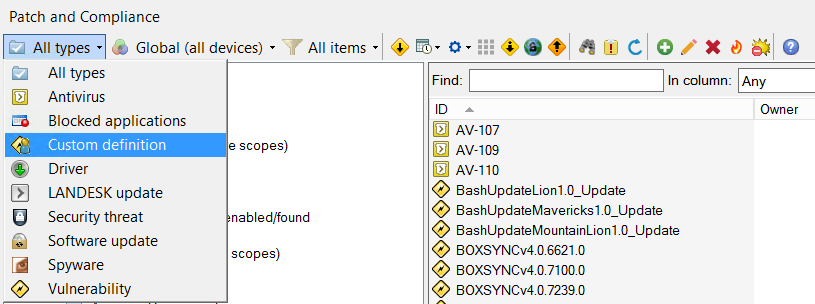
- In the white space area, right click and select Import
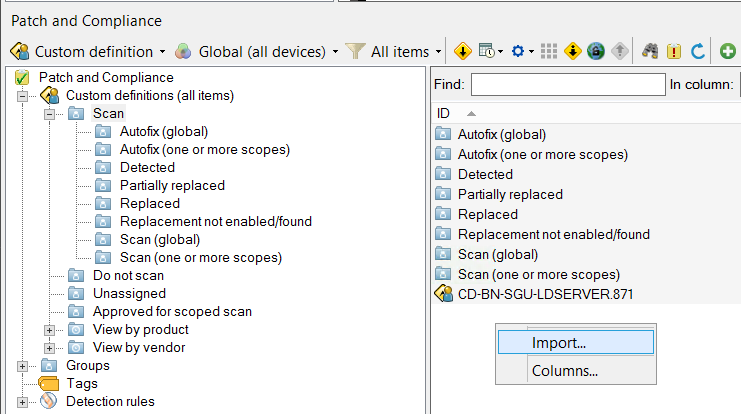
- Browse to the custom definition file and click the Open button to import
Once imported, set the definition to Autofix and it will maintain the AutoBoot state for you. It’s that easy to maintain, pretty nice, isn’t? It doesn’t matter if a person changes the value themselves, using Autofix it will continually set the value back to the state defined in the defintiion.
Understanding the Custom Definition
If you’re like me and want to understand how I built the custom definition, as opposed to just blindly importing the file I created, then read on.
There are 5 basic steps to building a Mac custom definition. First, you need to create the custom definition and add in the Properties Details. Secondly, you need to create a detection rule and set the affected platform state. The third step is to provide a script to do the detection work, add that to the Custom Script panel. The forth step is to specify the repair process in the Patch Information panel. Lastly, you need to provide Patch Install Commands to make the changes necessary if you initiate a repair.
- Create a custom definition by clicking on the green circle with a white plus symbol when inside the Custom Definition dropdown panel
- Enter in your desired information on the General tab and Description tab, like the severity and notes around what the custom definition will do.
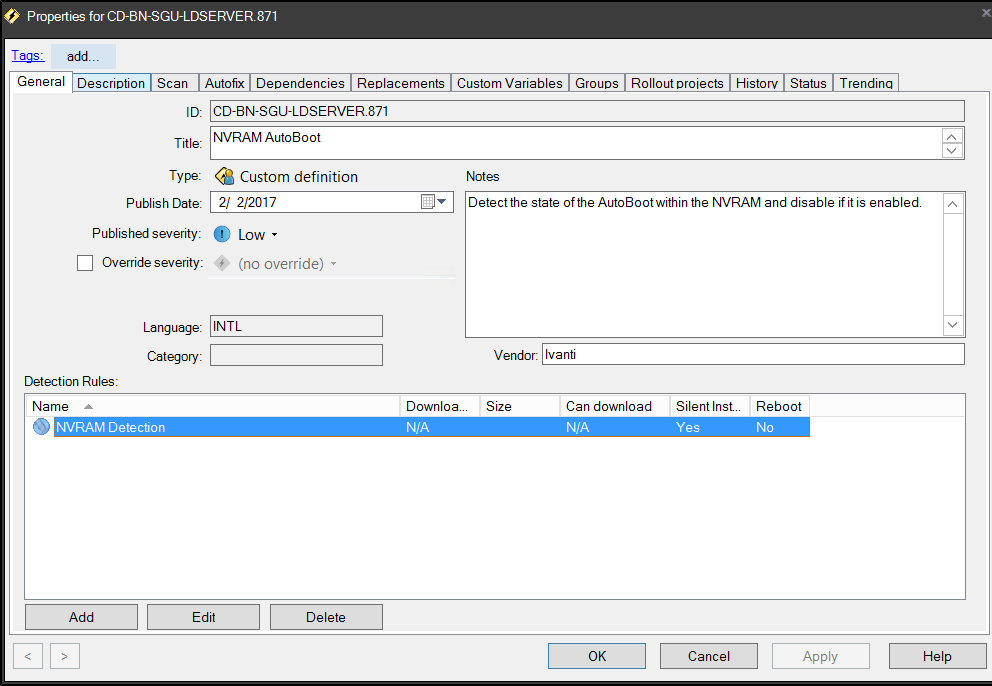
- Click the Add button under Detection Rules panel and specify your Affected Platforms. I check both Mac OS X and Mac OS X Server.
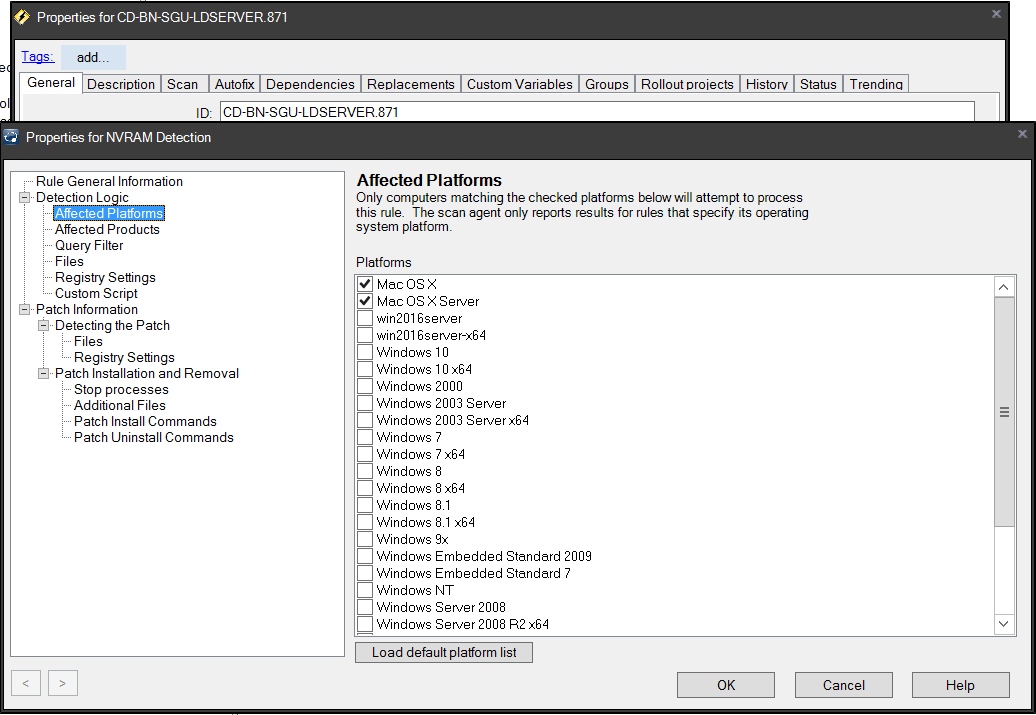
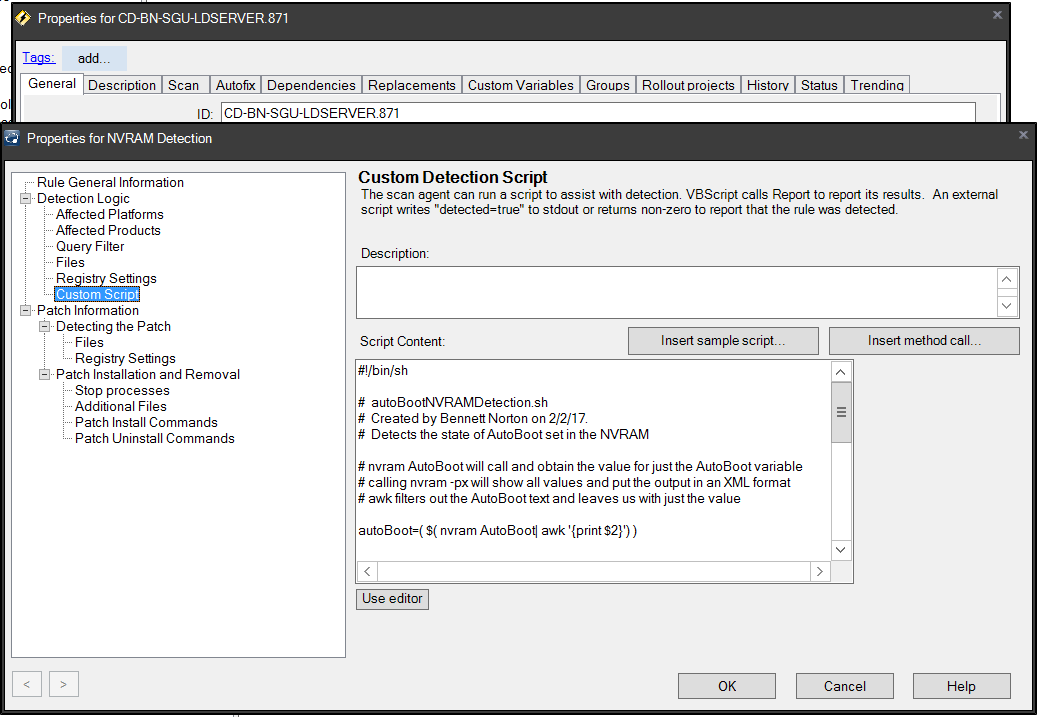
- Now you need to add in your detection logic in the Custom Script panel. For the AutoBoot feature, we really only need two lines. We need to specify the shebang environment and we need to capture the AutoBoot value. Now, I have added a few extra lines for documentation, which you can leave to assist your coworkers. My scripts are all pasted below or available on GitHub. Also, in every custom definition, you need to return the Found state, Reason state, Expected state and a Detected State of either 0 or 1. I don’t get into the details of this, so for more info see the Interchange Presentation regarding Custom Definitions.
- Finally, we need to add in the repair logic on the Patch Install Commands.
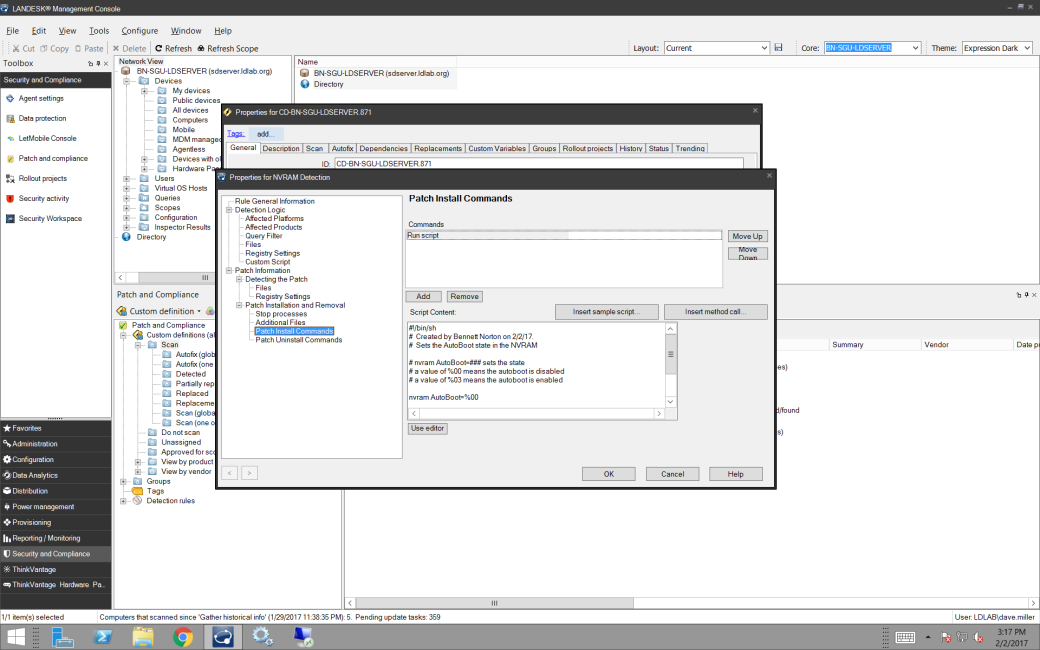
That’s all there is to it. Just hit OK at this point.
Now, if you’re wondering why I didn’t add in some Uninstall logic to revert our change back, if we desire, it is because the Mac agent doesn’t support it at this time. Feel free to put in a request with Product Management if you think this would be helpful.
Scripts
Detection Logic
#!/bin/sh
# autoBootNVRAMDetection.sh
# Created by Bennett Norton on 2/2/17.
# Detects the state of AutoBoot set in the NVRAM
# nvram AutoBoot will call and obtain the value for just the AutoBoot variable
# calling nvram -px will show all values and put the output in an XML format
# awk filters out the AutoBoot text and leaves us with just the value
autoBoot=( $( nvram AutoBoot| awk '{print $2}') )
# compare the nvram state with your desired state
# a value of %00 means the autoboot is disabled
# a value of %03 means the autoboot is enabled
# any other value means the autoboot state is undefined
if [[ $autoBoot == *"%00"* ]] ; then
echo "Found: NVRAM AutoBoot value is $autoBoot"
echo "Reason: NVRAM AutoBoot value is $autoBoot"
echo "Expected: NVRAM AutoBoot to be disabled or set to %00"
echo "Detected: 0"
exit 0
else
echo "Found: NVRAM AutoBoot value is $autoBoot"
echo "Reason: NNVRAM AutoBoot value is $autoBoot"
echo "Expected: NVRAM AutoBoot to be disabled or set to %00"
echo "Detected: 1"
exit 1
fi
Disable Logic
#!/bin/sh
# autoBootNVRAMDisable.sh
# Created by Bennett Norton on 2/2/17.
# Sets the AutoBoot state in the NVRAM
# nvram AutoBoot=### sets the state
# a value of %00 means the autoboot is disabled
# a value of %03 means the autoboot is enabled
nvram AutoBoot=%00
Enable Logic
While I don’t use the next script in the custom definition, if you wanted to enable the setting for all machines, you’d use this script instead.
#!/bin/sh
# autoBootNVRAMEnable.sh
# Created by Bennett Norton on 2/2/17.
# Sets the AutoBoot state in the NVRAM
# nvram AutoBoot=### sets the state
# a value of %00 means the autoboot is disabled
# a value of %03 means the autoboot is enabled
nvram AutoBoot=%03



















Recent Comments